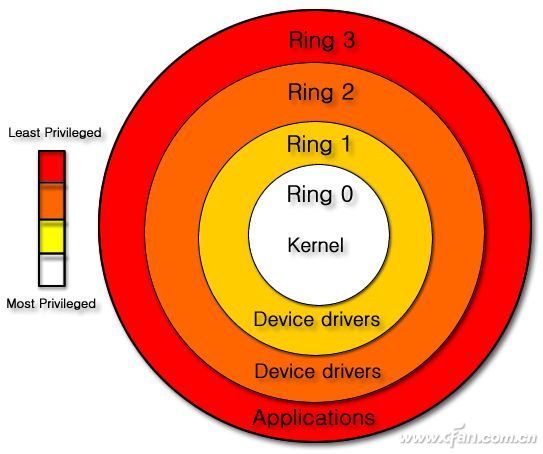
The recent news about CPU vulnerabilities has been quite shocking. It's hard to believe that one of the most essential and trusted components in our computers actually has hardware flaws! The main task for PC manufacturers right now is rolling out software patches to fix these hardware issues. However, these fixes often come at the cost of reduced CPU performance. But what exactly are these vulnerabilities affecting? Should you be worried? The Vulnerability Is Real, But Not Something to Fear Yes, the vulnerability exists, but there’s no need to panic. These flaws have been around in CPUs for over a decade, though the technical details were not widely known until recently. In fact, Google’s Project Zero team discovered several chip-level vulnerabilities last year, including "Spectre" (CVE-2017-5753 and CVE-2017-5715) and "Meltdown" (CVE-2017-5754), which are caused by speculative execution flaws. These vulnerabilities allow non-privileged users to access system memory and potentially read sensitive data, such as passwords or private files. After further investigation, it was confirmed that Intel, AMD, and ARM processors are all affected. This means that both desktop and mobile systems—whether running Windows, Linux, macOS, or Android—are at risk. However, it's important to note that this is still a potential threat, not an active one. What Exactly Is CPU Privilege? Most modern CPUs use a protection ring system to manage access to different levels of resources. For example, Intel x86 CPUs have four rings: Ring 0 through Ring 3. Ring 0 is the most privileged and is typically used by the operating system kernel, while Ring 3 is where regular applications run. Operating systems like Windows, Linux, and Android usually only utilize a few of these rings, with most applications running at Ring 3. Some CPU instructions are considered dangerous and can cause system crashes if misused. These are reserved for the OS and its drivers, not for everyday apps. If a program could bypass these restrictions and access Ring 0, it would pose a serious security risk. Fortunately, so far, no real-world attacks have successfully exploited this flaw. Intel has had similar issues before, such as the infamous Management Engine (ME) vulnerability. Unlike the current issue, the ME was based on Ring -3, giving it near-complete control over the system. While patches exist, they only affect older Core i3/i5/i7 models from the 4th generation. The scope was much smaller compared to the current Spectre and Meltdown issues. While CPU privilege management is crucial, most ordinary users don’t need to worry too much. At this point, there’s no widespread exploitation of these vulnerabilities, and the technical details remain largely undisclosed. That means the immediate risk is low. However, businesses and organizations should definitely apply the necessary patches. For home users, weighing the performance impact of the patches might be a more practical approach than rushing to install them. Overall, while the vulnerabilities are real, they don’t pose an immediate danger to most users. As always, staying informed and taking reasonable precautions is the best strategy.
Medium Voltage Power Cables includes Single Core Medium Voltage Cable, Three Cores Medium Voltage Cable. They are used for power networks, industrial plants.
Generally, Medium Voltage Cables are Copper Wire conductor, Semi-conductor Shield, XLPE insulation, Semi-conductor Shield, Steel Wire Armored or Steel Tape Armored, with PVC sheath or LSOH Sheath.
We supply lots of those Cable as per IEC 60502 and other requirements. BDK is top supplier for China Southern Power Grid.
Medium Voltage Power Cables,Medium Voltage Cable,Cable Medium Voltage,Mv Cable Shenzhen Bendakang Cables Holding Co., Ltd , https://www.bdkcables.com